In this week’s digest, we’ll discuss the following:
- Linux NetFilter use-after-free Kernel Vulnerability
- WordPress Core v6.2 XSS/CSRF/Directory Traversal Vulnerabilities
- Linux OverlayFS Vulnerability
CVE-2023-32233: Linux NetFilter Kernel Vulnerability
Background
NetFilter, is a framework for packet filtering and network address translation built into the Linux kernel for managing network traffic. It’s controlled by userspace utilities like iptables, UFW, and nft. Both iptables and nftables are based on NetFilter, with nftables being the more modern implementation. System administrators use these tools to configure local firewall rules and monitor network traffic.
Vulnerability
The vulnerability, tracked as CVE-2023-32233, is a use-after-free vulnerability in the “nf_tables” module of NetFilter. “nf_tables” is enabled by default on most Linux operating systems. “Nf_tables” accepts invalid configurations, which become problematic in some scenarios when an invalid batch operation is performed. If the invalid batch operation is crafted in a specific way, it can lead to a corrupted internal state within the Linux kernel. This happens because the “nf_tables” module does not properly handle anonymous sets (a type of set without a name that is allocated an identifier by the kernel).
The corrupted state can be exploited to perform arbitrary reads and writes of kernel space memory. This can be utilized to escalate privileges for the local user. All versions of the Linux kernel prior to version 6.3.1 are vulnerable to this exploit.
It should be noted that an attacker needs access to a Linux system established before attempting to exploit this vulnerability. Additionally, they must have CAP_NET_ADMIN permissions and the ability to manipulate NetFilter directly via the third party API.
The impact of this vulnerability is high, as it affects a module enabled by default on many Linux operating systems. Additionally, a proof-of-concept has been released, which increases the likelihood of this vulnerability being exploited in the wild.
Mitigation
- Updating the Linux kernel on your systems to version 6.3.2 or higher is highly recommended
- Disable unprivileged user namespaces
WordPress Core v6.2 XSS/CSRF/Directory Traversal Vulnerabilities
Background
WordPress is composed of multiple parts: Core, Database, Themes, and Plugins. WordPress Core is the foundation of the rest of the WordPress platform and enables all the administrative and management functions.
Vulnerabilities
WordPress Core v6.2 has several vulnerabilities we will cover.
CVE-2023-2745: Directory Traversal
This vulnerability, tracked as CVE-2023-2745, allows an attacker to perform directory traversal over a WordPress site through exploiting the “wp_lang” parameter. Attackers can access and load arbitrary language translation files. Additionally, if an attacker has sufficient access to upload translation files, this vulnerability also can be utilized to perform Cross-Site Scripting.
CVE Pending: Cross-Site Request Forgery (CSRF)
This vulnerability, which does not have a CVE ID at the time of writing, is caused by the lack of nonce validation on an AJAX function. The AJAX function, called “wp_ajax_set_attachment_thumbnail”, can be abused to allow for unauthenticated users to update files associated with attachment thumbnails. This only can happen if an authenticated user performs an action, such as clicking a link.
WordPress has determined that this vulnerability is unlikely to be exploited in the wild, due to a complex series of events required in order for exploitation.
CVE Pending: Cross-Site Scripting (XSS)
This vulnerability, which does not have a CVE ID at the time of writing, is caused by improper validation of protocol when processing the response from oEmbed discovery. oEmbded is a format type in WordPress that allows for the rendering of URls from third-party sites. Typically, this is used when a user links another site in a comment, resulting in a preview of the linked site. Attackers that have contributor and above permissions can craft a malicious oEmbed payload at a third-party URL that will cause arbitrary scripts to be executed when a user accesses that third-party URL.
NOTE: The original patch for these vulnerabilities, version 6.2.1, also fixed a minor vulnerability with shortcodes. The fix for the shortcode vulnerability broke functionality. In version 6.2.2, this issue is fixed.
Mitigation
- Updating WordPress to version 6.2.2 or above is highly recommended.
CVE-2023-0386: OverlayFS Vulnerability
Background
SetUID is a special file permission that allows any user with execution permissions to execute a binary as the user or group that owns the file. In the case that the SetUID bit is set on a binary owned by root, any user with execution permissions can run that binary as root.
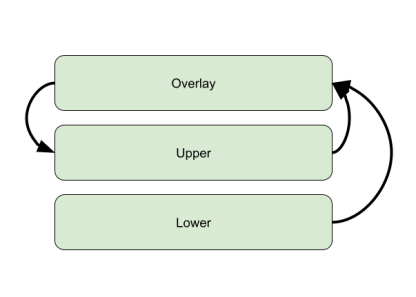
OverlayFS is a way to merge several mount points on a Linux file system, into one unified file system. It consists of several layers: lower, upper, and overlay.
- The “lower” layer contains the base mount points for your pre-existing data. Data is accessible upstream in the overlay layer.
- The “upper” layer is defined as part of the overlay filesystem. All files written to the overlay layer are copied to the upper layer. When files are changed in the lower layer, the changes are propagated to the overlay layer, and then the upper layer.
- The “overlay” layer is the top layer of the filesystem. It is composed of files from the upper and lower layers. All files can be accessed from the overlay layer.
Here is a simple diagram that shows how file changes are propagated through OverlayFS:
Vulnerability
This vulnerability is tracked as CVE-2023-0386, all versions of the Linux kernel prior to 6.2-rc6 are vulnerabile. When adding a file to an OverlayFS filesystem, the overlay layer does not properly check the user/group validity in the current namespace before copying it to the upper layer. An attacker can add a binary with the SUID bit set to a lower layer, and then have a binary copied to the upper layer.
An attacker can create a new virtual filesystem and namespace, generate an SUID binary with ownership as root, and then mount it into an OverlayFS filesystem. The OverlayFS filesystem won’t check if the user/group ownership is valid in the current namespace, and copy the binary with permissions intact. The attacker can then execute the SUID binary from the upper layer and elevate their privileges.
Mitigation
- Updating the Linux kernel on your systems to the latest version is highly recommended.
- Disable unprivileged user namespaces.




Comments